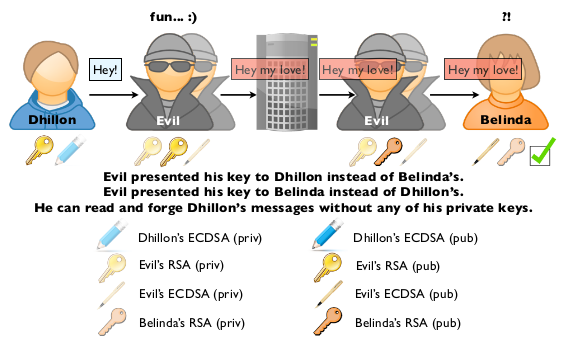
The assumed interception message allows the scammers and attackers to seamlessly change the sent message before it arrives and thereby impersonate the sender. Apple’s claim that“iMessage is not architected to allow Apple to read messages†is now brought into question as the researchers released video evidence of the vulnerability…
French security researchers Pod2G and GG allowed ZDNet to film an exclusive demo of them intercepting, reading and changing the content of iMessages between two iPhones, have a look below.
As you can see in the above video, both devices were running on iOS 7.
This is Apple’s statement issued in June in response to the NSA snooping (emphasis mine):
Conversations which take place over iMessage and FaceTime are protected by end-to-end encryption so no one but the sender and receiver can see or read them.
Apple cannot decrypt that data.Similarly, we do not store data related to customers’ location, Map searches or Siri requests in any identifiable form.
“Apple’s claim that they can’t read end-to-end encrypted iMessages is definitely not true,â€QuarksLab’s white paper reads. “As everyone suspected: yes they can!â€
Performing such a man-in-the-middle attack, however, would require someone with superior skills, substantial resources and physical access to your device.
The researchers explained that to break iMessage encryption in the manner shown would require the attacker to get physical control of the device — once.
Then, the attacker would install fraudulent certificates on it, and run spoofed servers tricked out to mimic Apple servers. The flaw’s essence, as QuarksLab described it, lies in the protocol’s lack of certificate pinning.
According to a leaked memo by the United States Drug Enforcement Administration, its agents had found it impossible to “intercept iMessages between two Apple devices†due to strong iCloud encryption.